Traversing NAT Firewalls
July 16, 2013 Leave a comment
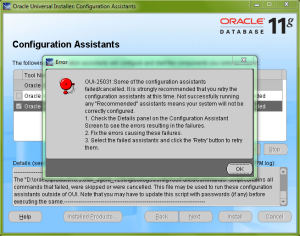
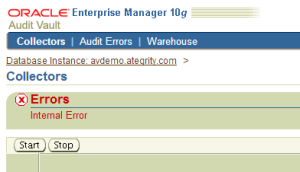
NAT Firewalls throw up a few interesting problems for an Audit Vault system. Due to the various network channels, a variety of solutions are needed, as each network channel differs in how it does address translation. In addtion to this, the target database will affect the way NAT is traversed.
There are three essential connections. The first connection required is that between the Audit Vault server and the Audit Vault Collection Agent. By default, the agent listens on port 7000 for connections from the Audit Vault server. The hostname or IP address is obtained by the server by querying the AVSYS.AV$AGENT table, and the hostname is then resolved on the server (if necessary). The agent also has to be able to connect to itself in order to be installed or started. This means that the hostname/IP address must be resolved locally on the agent machine too. Due to NAT, the IP address cannot be used*, so a hostname must be used. This hostname must resolve to the external IP address on the Audit Vault server, and to the internal IP address on the agent host. The simplest method of achieving this is to alter the hosts file on each machine to add a unique entry.
* Technically, the IP address can be used by using the internal IP address and creating a forwarding rule on the Audit Vault server that redirects traffic to the external IP address when the internal IP address is the destination. This is required for non-Oracle databases. Note that you can still use the hostname method if the Audit Vault server resolves the agent hostname to the internal IP address.
The second connection required is from the agent to the listener on the Audit Vault server. By default, this will be port 1521 on the Audit Vault server. These connection details are stored in the tnsnames.ora file in the agent’s Oracle home. As such, the external IP address of the Audit Vault server can be used, or a hostname that resolves to the external IP address.
The third connection required is from the agent to the source database. This is where the method differs between Oracle and non-Oracle source databases. For Oracle databases, the same method as for the first connection is needed*. This is because the agent must be able to connect locally to the source database, so it must resolve the address to the internal IP address, and the Audit Vault server needs to be able to connect to the external IP address in order to do audit policy management and gather entitlement snapshots.
For non-Oracle source databases, a connection does not need to be made from the Audit Vault server to the source database. The agent needs to connect to the source database, though, and in order to do so, the agent queries the Audit Vault server to obtain the source database connection details. The big issue here is that the Audit Vault server will resolve the hostname before sending it to the agent, so the server must resolve the hostname to the internal IP address of the source database. This puts it at odds with the first connection, which requires that the server resolve the hostname to the external IP address!
The solution is to set up forwarding on the Audit Vault server which redirects all traffic destined for the source database’s internal IP address to its external IP address, and to use the internal IP address (or a hostname that resolves to the internal IP address) for all connections.
* If entitlement snapshots and/or audit policy management are not required, then the internal IP address, or a name that resolves to the internal IP address, can be used.
As you can see, there are a few issues with traversing NAT but they can all be resolved.